During times like these, it is more important than ever to try to limit extra strain on resources. One way that we can do that is to decrease the likelihood of having to spend time and money either redoing a sampling event or recollecting data. This can be accomplished by producing quality and defensible data.
When organizing a project sampling or data collection event, defensibility of the collected data may not always be amongst the top factors considered. However, if the validity of the data eventually comes in question, data defensibility quickly becomes the most important aspect of the project. Data defensibility, like safety, should not be left to chance; nor should it be an afterthought.
Data end users make assumptions and conclusions based on data collected during the course of field activities. This might include closing a site, remediation, additional sampling, risk conclusions, or more. While blatant fraud is a rare occurrence and certainly not the norm, it is not uncommon for data to be accidentally altered because of inappropriate field or laboratory practices. Anyone with a history in environmental data knows that human error is possible at any phase of data collection, analyses, review, or reporting. While most professionals do their best to eliminate these errors, a switched label, incorrect entry, or distraction can lead to thousands of dollars of recollection and reanalysis costs.
Good practices and check points can be added at many phases in the collection and analyses process, that will help eliminate common errors. Using tools such as checklists for sampling events, data validation, and defensible data management can help defend the data at critical stages during the project life cycle. Additionally, having a clear understanding of the ultimate data objectives and quality requirements prior to data collection serves to reduce issues. Trihydro’s Data Defensibility Guidelines walk through the process of defining, planning, preparing, executing, reviewing, and managing data in a way that is defensible.
Steps to Data Defensibility
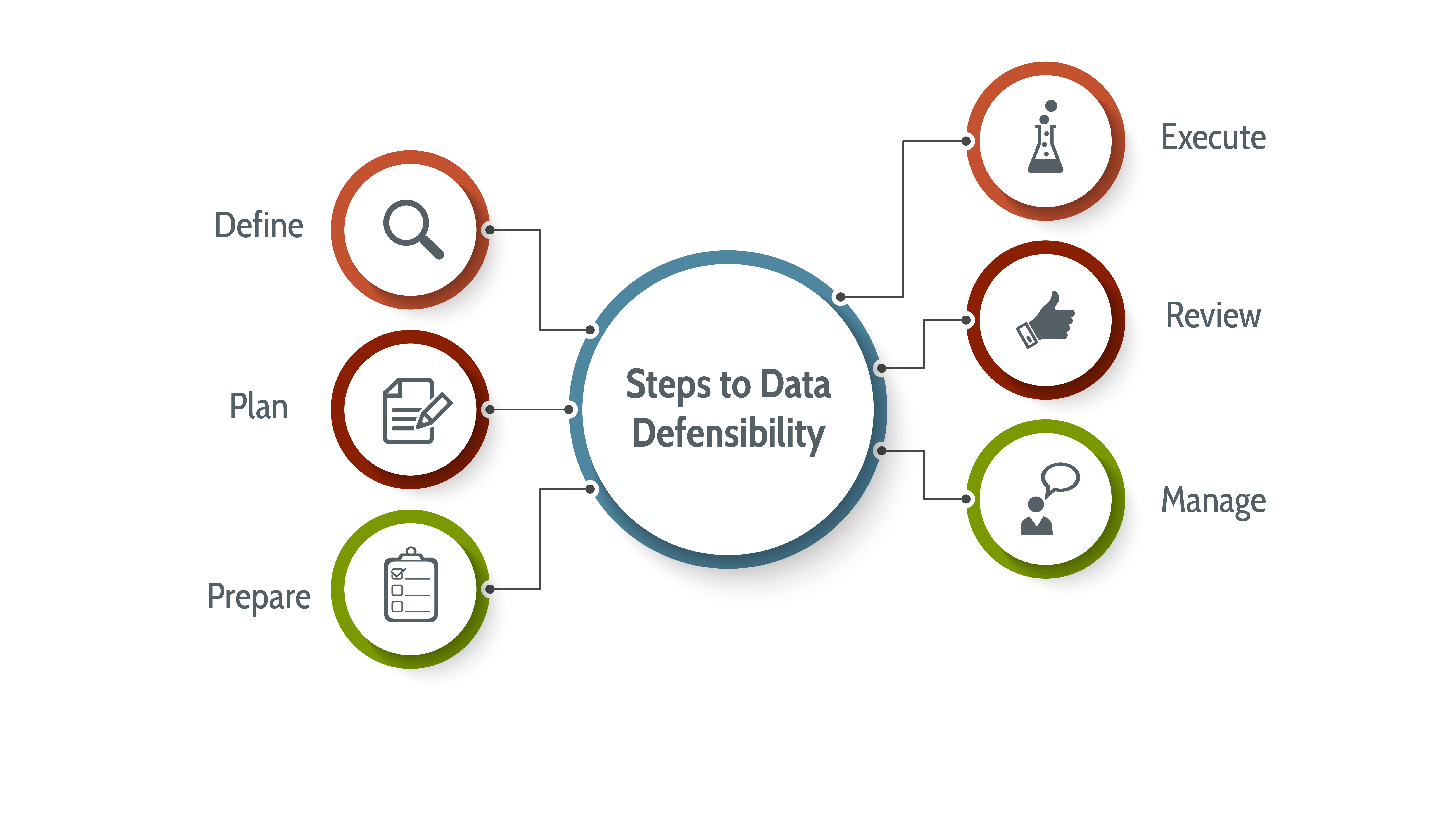
- Define: The first step in planning for legally defensible data is defining what will make your project successful. Understanding the final goal of your project and how the collected data is to be used will help focus inventory of the data needed to produce and evaluate the specific needs associated with your project.
- Plan: Choose project tools that support your success. This includes developing data quality objectives (DQOs) and determining which planning documents you will use (i.e., SAP, QAPP, DMP, SOPs, FSP, etc.) to measure the defensibility of your data. The most important aspect of this stage is to communicate project success requirements to the laboratory, managers, and sample crew and get their input.
- Prepare: Preparation of what tools will be used to measure the defensibility are initiated prior to sample collection. The most important aspect of planning will be to effectively communicate project success requirements to the laboratory, managers, and sample crew.
- Execute: Confirm samples are collected in accordance with the planning documents. Chain-of-custody should be properly documented and maintained, and the laboratory should analyze the data in accordance with approved methodology.
- Review: The review process validates plans have been followed and executed in accordance with what was initially proposed and approved.
- Manage: Following review, approve or reject data, as necessary. Data must be maintained with data validation and laboratory data qualifiers, as well as associated notes.
Stepping through this process systematically will help to increase your confidence in producing defensible data capable of withstanding technical or legal scrutiny. If you need assistance verifying the defensibility of your data, we can help. Download our Data Defensibility Guide to get started today!
